Better cyber security–more considered, more connected.
We’re a team of seasoned Cyber Security Specialists who help organisations mature their cyber security and navigate compliance. Our goal is for those at the helm of scaling businesses to get a better night’s sleep knowing they’re fortified online. Whether you need a little guidance on direction or a complete team to do the bulk of the lifting, we can help.

More considered
We believe in a considered and custom approach to cyber security, not some generic, cookie-cutter plan. That means really considering your people, products, processes etc, so we can build something as practical as it is protective.
More connected
We’ve built our cyber security team to connect right into your organisation, allowing us to handle as much or as little of the load as you need. We use agreed monthly hours to scale your cyber security as your organisation grows.



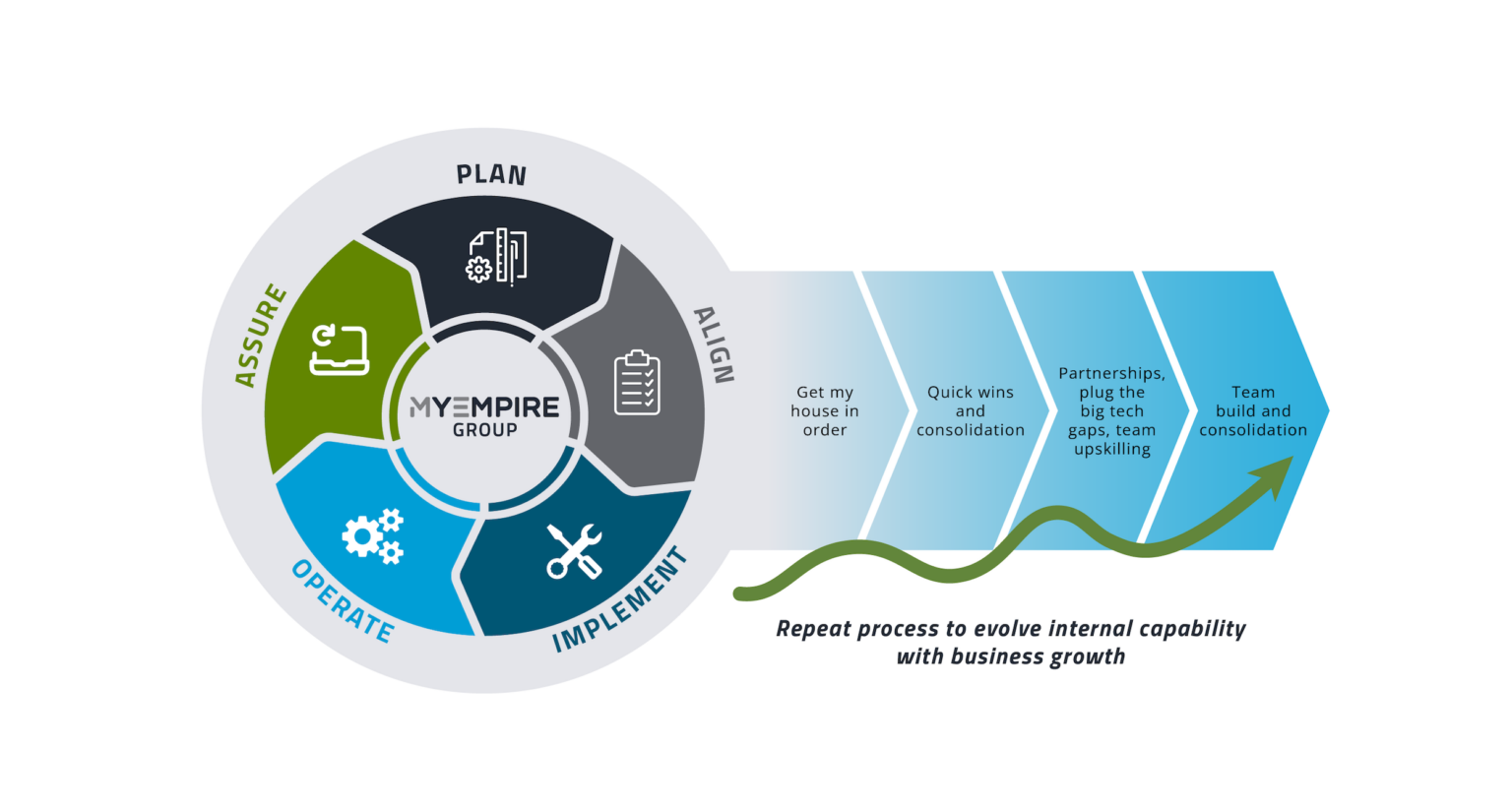
Mature your cyber security
Improve your organisation’s risk posture from the top down. By spending time getting to know your business, we design and build a cyber security strategy that genuinely fortifies your business online, not just on paper. We also learn where your business is heading so we can bolster your cyber security as it scales.


Guidance through compliance
Our Governance, Risk and Compliance specialists are not only experts in cyber regulation—fast-tracking you through the process—but they’re excellent communicators. It means, as well as showing you a clear path through compliance, we thrive at educating your team to ensure your whole company is on the same page.
Leadership obtaining certifications
Looking to obtain a cyber security certification such as ISO 27001 or Cyber Essentials, or to align to another such as Essential 8 or NIST? We’ve guided many businesses through the steps required to gain certification and can ensure the process is as productive and stress-free as possible.

Talk to a Cyber Security Specialist